An Introduction to Network Addresses
Article by Steve Fryatt
WROCC’s September 2009 meeting saw us take a whistle-stop tour through the subject of networking and afterwards, we promised – perhaps foolishly – to look at it in more depth. This HowTo was the first in a series of articles which were subsequently published in the club’s newsletter, The WROCC. It can now be found as one of the twelve articles that form The WROCC Guide to Networking, which is available to purchase from the Club in A5 printed or PDF form.
Separating the parts
At its simplest, a network is a means of connecting a collection or computers – or devices which contain computers – together so that they can share data and resources. Along with basic desktop PCs, all kinds of other devices can be connected: printers, file-storage units, ADSL and cable modems for internet access, MP3 players. The list is almost endless.
Networking hardware comes in two main flavours: wired and wireless. Most of us are probably familiar – at least by sight – with wired networks: Cat 5 cables ending in RJ45 connectors. This is what you will get if you order a modern network interface card for a RISC OS machine; the older co-axial leads with the round BNC sockets are obsolete these days. The other option is wireless: laptops, routers, mobile phones and PDAs often have this included.
However, once it’s set up and working, the complexity of how all the bits of hardware talk to each other becomes invisible to the computers using the network. It doesn’t matter whether your network uses Cat 5 cable, wireless links, mains-borne HomePlug connections or even any combination of the three – once the connections have been made, the devices on the network can all be treated and configured in the same way.
In some ways, RISC OS users have it easy. Our machines tend to come with wired network ports and no wireless option, so connecting things together is simple as long as enough Cat 5 cable is available. As a result, I won’t be mentioning the kind of connections much in this HowTo.
A simple network
The simplest network consists of two machines, connected by a single cable (as shown in figure 1 below). Modern network cards may be able to do this with a standard network cable; older ones will probably require something known as a ‘crossover cable’. The two machines can talk to each other, but that’s it.

Figure 1: A very simple network
To add anything else, we need an additional piece of hardware known as a ‘switch’ or a ‘hub’ – switches are better than hubs (for largely technical reasons that won’t worry most home users), and these days you will have to search very hard to find anyone still selling the latter. Adding a third computer is simply a case of connecting each one to a central switch, using standard Cat 5 network cables: this is shown in figure 2.
Figure 2: A network with some more devices
As long as you don’t need to connect to the internet, or anyone else’s networks, then this setup is all that is required for a simple home or office use. All of the computers can see all of the others, and as long as suitable software is installed, they can share files, printers and more besides. However, we need to be able to identify which computer is which, so the next step is to give each of them a unique ‘tag’ – an address.
Addressing the issue
On all but the simplest of networks, all the devices will have a couple of different addresses: an IP address and a MAC address. MAC addresses are unique to a device, and belong to that device from the time of its manufacture; IP addresses, on the other hand, will still be unique for every device connected to the network, but the address a device has may change many times in its life, depending on where and when it is connected.
To use an analogy, a MAC address is a bit like a person’s name: it uniquely identifies the person in question, and they will often keep their name from birth. An IP address, meanwhile, is like their home address: it uniquely identifies where they can be found at any given point in time, but is subject to change if they move house.
MAC addresses are 48 bits long, and chunks of addresses are allocated
by the IEEE to manufacturers of network hardware. For human convenience,
they are usually written down as six pairs of hexadecimal digits, and
often appear as 12-34-56-78-90-ab or 12:34:56:78:90:ab. On a RISC OS
machine, the MAC address of the network interface can be found using the
*ifconfig -a command.
Due to their ‘permanent’ nature, MAC addresses are often used by network hardware to identify actual devices on the network. An example of this would be a wireless access point only allowing access to devices whose MAC addresses have been added to a list of ‘allowed’ machines. If you configure your wireless router to recognize only your laptop’s MAC address, for example, then your neighbour can’t connect using their computer.
The right protocol
When data is being routed around a network, however, it’s IP addresses – not MAC addresses – that are used to arrange delivery. Rather like postcodes in conventional mail there’s a logic to the numbers, and hardware in the network knows how to use this to direct the information along the correct wires.
Rather like MAC addresses, IP addresses are just a binary number – only they are 32 bits long instead of 48 bits (although this isn’t always true – IPv6 addresses, which RISC OS doesn’t support, are 128 bits). For human consumption, they are usually split into blocks of 8 bits and written as four numbers: for example 192.168.0.7 or 10.1.0.203.
To ensure that data gets delivered to the correct computer, every machine on a network must have a unique IP address allocated to it. This only applies to things that can have data delivered to them – things like switches and hubs, which merely pass packets through on their way somewhere else, don’t need one.
In order to do anything useful with your network, you will need to allocate each machine on it an IP address. Just like MAC addresses, these are given out by a central body – in this case the IANA; fortunately, there are several blocks of addresses allocated for use on ‘private networks’. The most common of these are in the range 192.168.x.x and 10.x.x.x.
There are a number of different ways that addresses can be given to devices. Until recently, RISC OS systems had to have the addresses set manually by the user; now, depending on what else is on the network, the job can be done automatically. We’ll come back to this in a later HowTo.
Sub-networks
In order to route data around the network, and on to other networks, IP addresses are split into two parts: one identifies the network, while the other specifies individual machines on that network. The number of bits either side of the divide varies depending on the network concerned, and its location is given by something known as the ‘subnet mask’.
Subnet (or just ‘net’) masks are usually written in the same style as IP addresses, and the most common one on home networks is ‘255.255.255.0’. Viewed in binary, the bits of the mask that are set indicate bits in the IP address which refer to the network; those which are unset show the bits that identify the individual machines. So with this net mask, the address 192.168.0.7 points to machine 7 on network 192.168.0. Figure 3 shows this more graphically.
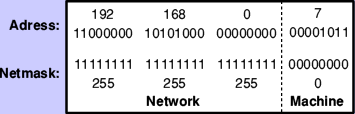
Figure 3: The make-up of an IP address and netmask
As home networks normally use the netmask 255.255.255.0, all the devices connected to them must use addresses with the same first three sets of numbers. These need to fall into those ranges allocated by IANA to private networks, but beyond that it’s up to you (using the same network that your broadband router’s default is in, if you have one, is a good idea).
Since IP addresses and netmasks often need to be given together, there are a number of different forms available to write them down. The long-winded approach is to write each out in full: ‘192.168.0.7/255.255.255.0’. This is clearly a mouthful, so it’s common to see the shorter version: ‘192.168.0.7/24’ – the ‘/24’ is a way of showing that the first 24 bits of the netmask are set.
Finally, there are two special machine numbers to be aware of: that with all its bits unset, and that with all its bits set. These should not be used for devices on the network, as they have special meanings; in the network above, these would be 192.168.0.0 and 192.168.0.255. This gives a useful range of machine numbers from 1 to 254 on the average home network.
Escaping the net
On a simple, self-contained network consisting of a number of machines connected by one or more hubs or switches, all of the IP addresses must be on the same network number, and all of the netmasks must be the same. If they are not, then things will very quickly go wrong.
In order for two machines on two networks using different netmasks or network numbers in their IP addresses to communicate, a piece of hardware called a ‘router’ is required to sit between them. This has two network connections, one on each network, and it passes packets of data back and forth. A router could easily be a computer with two network cards and the right software installed – each card having a different address.
If you have ADSL or cable internet and it connects to your computer via the network port, then your broadband modem will also be a router: it will be transferring packets between your home network and that which your ISP is operating. However, because home networks will be using one of the private address ranges, it will also be performing a function called Network Address Translation, or NAT.
Without NAT, if machine 192.168.0.2 in figure 4 contacted 87.204.78.92, then each would know the address of the other. Unfortunately, since addresses from the public ranges will be in use all around the world, there could be many millions of 192.168.0.2s connected to the internet at any one time with no way to tell them apart.
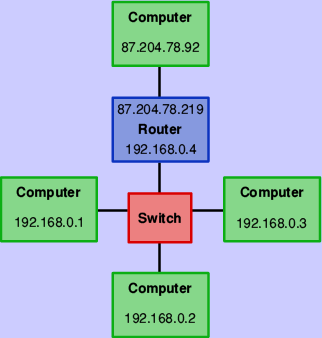
Figure 4: Linking two networks with a router
So that packets return to the right place, the broadband router uses NAT to remove all references to the private address (that is 192.168.0.2) before sending the data on to 87.204.78.92, making it look as if the information really came from the router itself – the router’s address of 87.204.78.219 isn’t from a private range, and so will be unique on the internet. If a reply comes back from 87.204.78.92, the router remembers which machine on its private network sent the original request, and forwards the information on.








